THE BEST WAY TO DOWNLOAD TORRENTS FASTER OR ANY OTHER HEAVY FILES
I came a cross a service called offcloud as i was suching for ways to download torrent files faster through my download manager and securely and i landed on that awesome serivce called offcloud
when you sign up your given a free trail of 3 links which you can use to upload content from an site
in my case it was torrent sites and these links with the instant download option where u upload it and download it instantly and the cloud option where u can upload your files to their cloud and for futre download and The last option remote upload this option allows you to upload your files through
offcloud to your favority cloud storage service eg google drive,mega,dropdox.Follow this link and check them out it maybe the service you have been looking for
https://offcloud.com/?=7357fd48
Wednesday 21 June 2017
Chris Putnam : The First Facebook Hacker
If you’ve been a long time user of Facebook, you are sure to come across an emoticon of a man’s face facing upward to the right . If you have asked your friends or googled how to do it, you know that all you need to type is :putnam: for the emoticon to show. Have you wondered what putnam means ? Its not a word in the English language, so what could it signify ? That emoticon is the last name of a man named Chris Putnam and this is his story.- :putnam: doesn’t works any longer to show up as an emoji
The short answer – the one you will most likely find on the internet – is that Chris Putnam is an engineer at Facebook. The full story however, is a little more entertaining. At the end of this article, you will also realize that it wasn’t Putnam who added his emoticon to Facebook chat, it was his friends that did it.
Our worm code would rapidly and silently copy itself from profile to profile, spreading virally through friends viewing one another’s profiles. The code itself was run off of an off-site server under my control, so at any time I could change the script that was running on everyone’s profiles, says Putnam on his blog.Before seeding the worm Putnam and Marcel had co-written a JS library that could replicate some of Facebook’s functionalities including adding a friend, poking, messaging, wall posts, among others. This allowed them to modify the master script to carry out actions through the infected accounts. The first version of this worm would include this library and would also send a friend request to his test account thus, allowing him to easily track the number of infected users as the outstanding friend request number ticked up on his homepage.
During this time, his friends were working on a CSS stylesheet that would re-style a Facebook profile to look like a Myspace account ( as it looked in 2005). It would modify every single field on the profile and make it look exactly like a Myspace account including the colour scheme. Thus the first version of this worm would do 3 things
- It friended his test account
- It re-styled the profile to look like MySpace
- It copied itself to your own profile.
The modified profiles however, would barely last a day before the user complained to Facebook about the problem. This also led to a number of Facebook employees having their accounts infected including internal test accounts known simply as ” The Creator ” leading them to infer that they might have possibly infected the account of the Facebook founder ( since he was technically the creator ).
As fixes started rolling out for the worm, I got a message in my personal Facebook inbox from co-founder Dustin Moskovitz. His knowledge of my identity didn’t come as much of a surprise since the worm’s interaction with my account was a dead giveaway and we even went out of our way to provide contact information in the source code and CSS file. I’m having a hard time finding the exact text of his message right now, but it was along the lines of “Hey, this was funny but it looks like you are deleting contact information from users’ profiles when you go to replicate the worm again. That’s not so cool.”This led to a string of messages being exchanged between him and Dustin where he explained the worm in details along with other loop holes that he had discovered. In the meantime, Putnam was looking to get a job and move to Silicon Valley. In 2006, about a year later, he managed to get a job interview from a company based in Silicon Valley through a friend. When he mentioned this to Dustin, he was called for an interview at Facebook.
“Now, this seemed pretty nice and all, but this was a period in tech history where MySpace had just gone through something extremely similar–guy makes harmless XSS worm, company offers to hire him–but in their case, they had him arrested as he arrived at LAX and turned him into a convicted felon.”The Interview
With apprehensions in mind, he still went for the interview. He brought a friend along and stocked up on cash just in case things took a wrong turn. Until the moment when he entered Facebook’s offices and found Dustin waiting for him without cops, that he breathed a sigh of relief. The interview went off well and just a few days later, Putnam found himself employed at Facebook.
We end this piece with Putnam’s own words, ” I will be forever grateful that the company was so sympathetic toward people like myself. It’s one of the things that really sets Facebook apart with its passion for scrappy, hacker-type engineers”
Saturday 10 June 2017
How To Use RAM As Hard Drive? How To Create RAMDisk?
If you’re having an excess amount of RAM on your system, mostly unused, you can use it to create a RAM Drive or RAM Disk. You can take its advantage to reduce application load times, improve performance while playing games, or store 4K movies for better playback. There are various RAMDisk software available, both free and paid, which can be used to create and temporary or persistent RAMDisks. Getting a faster storage is every computer user’s dream. Most of the people now have the choice of using SSDs, but they are considerably costlier than the magnetic hard drives. However, if you have like loads of RAM sitting idle inside your PC, it can be a great source to construct some lightening fast storage media, even faster than the SSD.
What is a RAMDisk or RAM Drive?
RAMDisk is a term given to a virtual drive created on the system which uses the blocks on your physical RAM to store data. Early attempts to make storage media using RAM date back to 1980s. The development followed, and we actually have RAM-based hard drives. But these couldn’t go as viral as magnetic hard drives and later, SSDs, because of the high cost of the RAM storage and a continuous need to a power supply.Why use RAMDisk?
The reason why RAM is a separate piece of memory on your computer is because of its speed. Creating a RAMDisk would allow you save data on the fastest possible storage on your computer. It’s no denying the fact that you’ll notice a substantial reduction in the load times for programs you’ve have installed on a RAM drive. That’s because there is no need of transferring the files from your hard drive to the RAM.One of the important aspects of maintaining the RAM Disk is retaining data after you turn off your computer. RAM is volatile memory, and it can’t remember anything after the power goes off. So, all of the software and files you store on the RAM Disk are gone.
Now, here we find the need of RAMDisk software which in addition to creating the RAM Disk also stores the data onto your hard drive every time you shut down your PC and reloads it on the RAM Disk when you turn it back on. You can choose from a variety of RAM Disk software, and some of them have been benchmarked by Raymond.
In order to create a RAMDisk, make sure your computer has enough amount of RAM. This is because Windows OS needs around 2GB memory to function properly. And you have to leave a spare 1GB memory for other software. So, to create a 1GB RAMDisk you should have at least 4GB RAM on your computer.
Also, if you’re a running a 32-bit Windows, the maximum RAM it supports is 4GB. So, you don’t have a considerable window while setting up a RAMDisk. There is no such limit in the case of 64-bit Windows. So, if you have like 8GB or 16GB chip, then it’s easy to blow an 8GB RAMDisk inside your memory.
Also Read: 32-Bit Vs 64-Bit Windows OS: What Is The Difference? How To Choose?
How To Use RAM As Hard Drive In Windows 10? | Create RAM Disk
There is a number of paid and free RAMDisk software for Windows 10 and older versions. You might have heard about Dataram RAMDisk which is available in free and paid options. Here is how you can set up a RAMDisk using this software:- Install Dataram RAMDisk after downloading it using this link (scroll to the bottom of the web page).
- The default view is somewhat confusing. So, you can switch to View>Advanced if you want.
- Now, under the Settings tab, select the size of the
RAMDisk. It can only go up to 1023MB in the free version. However, the
paid version supports up to 64GB.
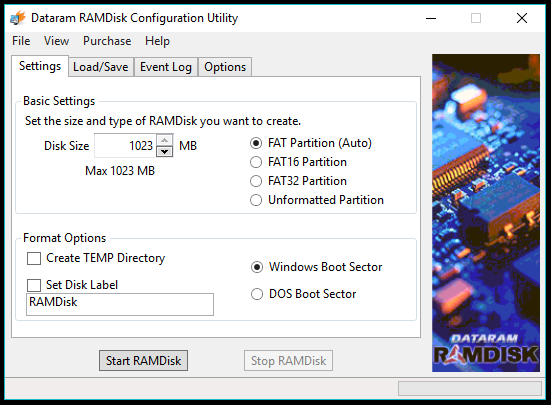
- Under the Load/Save tab, make sure Load Disk Image at Startup and Save Disk Image at Shutdown are ticked. This will make sure your files don’t evaporate when you shutdown the PC.
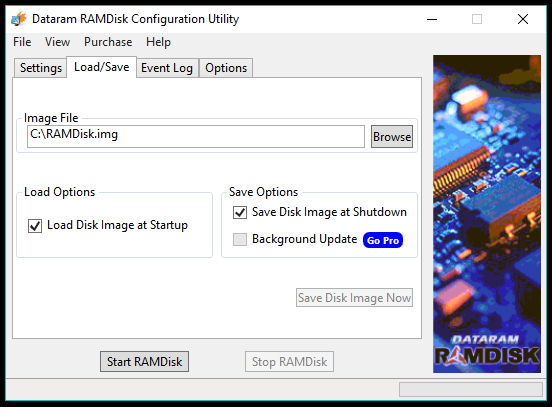
- Now you can explore the Options tab or click Start RAMDisk to get your virtual disk into action.
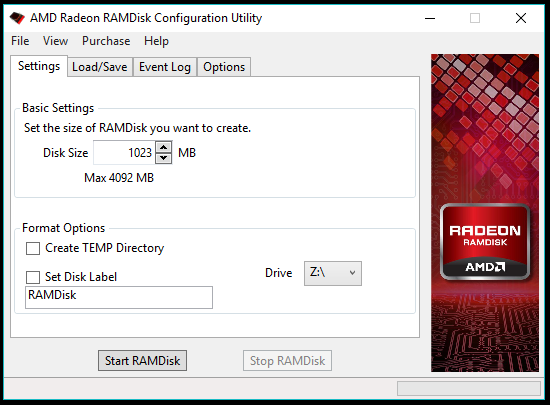
Dataram is easy but its 1GB limit is a serious drawback. AMD Radeon RAMDisk is an official variant of Dataram optimized for AMD-branded memory. But it still works with regular memory and increases the size up to 4GB (with 8GB RAM) for the free version. You can download AMD Radeon RAMDisk using this link. The user interface is almost the same.
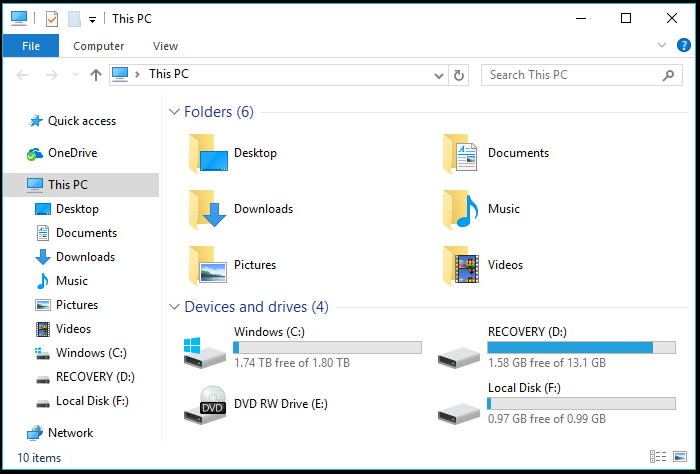
If you plan to uninstall Dataram RAMDisk, delete the image file located in root folder of your system drive, mostly C.
For those who want to go with a free and open source RAMDisk software, Imdisk is the answer. ImDisk promotes itself as a virtual disk driver instead. You can download ImDisk using this link.
After installation, ImDisk can be controlled using the CMD and it also appears as an applet in the Control Panel where you can access the application. Also, there is a modified version called ImDisk Toolkit which is more user-friendly.
There is no limit on the size of the RAMDisk but it comes at the cost of a tougher RAM Disk setup process. A sense of relief is you can create more than one RAMDisks on your computer.
Creating a RAMDisk using ImDisk’s GUI isn’t a rocket science, but the storage so created isn’t persistent. The moment you restart your machine, your RAMDisk is nowhere to be seen. You can follow the CMD-method detailed by a Guru3D forum user if you want to create a RAMDisk that can survive restarts and shutdowns.
Similarly, you can use some other RAMDisk software to take advantage of your extra RAM. You can install programs, games, or store any type of content you want to access quickly. However, one thing to note here is keeping a RAMDisk on a daily basis can slow down your shutdown and boot times. That’s because your machine will update the image file on the hard drive with the latest data present on the RAMDisk and the same will be loaded during startup. Most paid RAMDisk software update the image file in the real time so the problem is the case of the users shelling out cash from their pocket.
This was a brief overview of What are RAMDisks? Why do you need RAMDisks? And how can you create a RAMDisk and use ram as hard drive? If you found this helpful, drop your thoughts and feedback.
8 Best Anti Ransomware Tools You Must Be Using In 2017
In the recent past, ransomware has emerged as one of the most challenging cyber security threats. This has demanded the need for anti ransomware tools that one needs to use. Some of the notable tools like Bitdefender, Malwarebytes, Kaspersky, etc. use advanced methods to take preventive measures and block such attacks. Many ransomware removal and decryptor tools are also available for getting back your files. Over the course of past year, we kept telling you about different ransomware attacks, including the likes of Locky, Cerber, Jigsaw, KeRanger, etc. Many security experts also called ransomware the biggest threat we would see in upcoming months. This prediction came true with the arrival of WannaCry ransomware.
Top anti-ransomware tools in 2017
1. Bitdefender anti-ransomware and antivirus
In our article of top antivirus software of 2017, Bitdefender topped the list. The multidevice license of Bitdefender lets you select the preferred platform and enjoy advanced features like malicious URL blocking, on-demand scan, etc. But, what about ransomware protection?Talking about Bitdefender Antivirus Plus, it’s a complete suite that kills most types of Trojans, ransomware, and malware. Its ransomware protection in Bitdefender allows you to choose folders that one wants to be protected. This anti ransomware tool of Bitdefender comes with a flexible configuration as compared to other solutions. You can also use Bitdefender’s free anti ransomware tool that runs silently in the background provides protection against ransomware like WannaCry, Locky, TeslaCrypt, Petya, etc.
2. Malwarebytes anti-ransomware tool
In the recent times, while talking about best anti ransomware tools and anti-malware solutions, Malwarebytes appears towards the top of the lists. Due to the sophisticated nature of ransomware, many basic security software fail to prevent you. To save yourself from such threats, you need solutions like Malwarebytes.Malwarebytes 3, which promises to deliver all-round protection like Bitdefender, comes with a great anti ransomware tool that protects your files. Apart from ransomware threats, Malwarebytes also protects you from fake websites and links. It wraps the programs and browser into 4 defense layers and stops attacks that exploit different vulnerabilities. Last year, the company also launched Malwarebytes Anti-ransomware Beta.
3. Kaspersky anti ransomware tool
The reputed cyber security firm Kaspersky offers a dedicated tool to numb the ransomware infections. Created for keeping businesses and small organizations safe from ransomware, this tool is available as a free download. Just like most of the security suites, you don’t need Kaspersky Lab security suite to be installed on your computer. You can download this great anti ransomware software by visiting this link and add an extra layer of protection.Just like Bitdefender and Malwarebytes, the primary product of the company, Kaspersky Internet Security, comes loaded with anti-ransomware functionality. It also tells you about notorious websites and links to make your internet browsing experience even better.
4. Trend Micro Security
Trend Micro Security is another antivirus suite that comes with a great anti ransomware tool that minimizes the risk of infection. The latest release of Trend Micro antivirus comes with a strong focus on ransomware removal software and protects you from WannaCry ransomware.It comes with a Folder Field feature that adds an extra defense layer to files inside a protected folder. It prevents notorious ransomware from encrypting your files. The Folder Field feature prevents every process or service from accessing the file inside that particular folder. The company also ships Ransomware Screen Unlocker tool for ransomware removal from infected PCs.
5. Avast Antivirus
Ransomware malware are known for holding your important files in ransom and demanding money in return for access. So, one must use a reputed software to recognize, remove, and prevent ransomware. Consistently rated excellent by experts, Avast 2017 deals with prevalent threats like ransomware in an efficient manner.In Avast 2017, the company integrated AVG’s behavior analysis technology named Behaviour Shield. It sniffs the software for suspicious behavior and exposes the sample of ransomware by analyzing the code behavior. The company claims that Avast Behaviour Shield is capable of stopping new ransomware variants, which makes it one of the top anti-ransomware software around. Avast also provides multiple ransomware decryptors for removing ransomware and decrypting your files.
6. Zemana Antimalware
Based in Turkey, Zemana specializes in security for business and home users. They claim to make security programs with an easy-to-use interface for general users. After the initial launch of Zemana AntiLogger, the company launched Zemana AntiMalware which was designed to scan and clear a computer from malware. It also provides real-time protection and browser cleanup functions.Zemana Antimalware is based on its own signature database that removes the known and yet-to-be-born malware threats. One of the plus points of Zemana Antimalware is its lightweight and highly optimized nature that stores the virus definitions in the cloud to avoid cluttering the PC. In many independent security tests, including MRG Effitas, Zemana Antimalware was judged the best anti ransomware tool that one can use. It’s available in two versions. While the one with limited features is free, the commercialized version comes with a 14-day free trial.
7. McAfee Ransomware Interceptor
In the times like these where ransomware threats like WannaCry lock down people’s computers and demand ransomware, the need for an efficient anti ransomware software isn’t disputed. McAfee is a renowned name in the realm of cybersecurity. So, it would make sense for a McAfee product to make an appearance on this list of the best anti ransomware tools.Here, I’m going to tell you about McAfee Ransomware Interceptor (MRI). It’s an early detection tool that prevents the file encryption attempts made by a malware. By utilizing, machine learning and heuristics, this anti ransomware tool monitors and terminates the processes that resemble the characteristics of ransomware. Currently, this product is available for Windows 7 and later.
8. Tools to remove ransomware and decrypt files
In the points mentioned ahead, I’ll list some of the popular means to remove ransomware from your computer and decrypt files. These ransomware removal tools are useful when your computer is infected with ransomware and you need to get rid of them —- Nomoreransom.org website is backed by top security and tech giants. Here, you can upload encrypted files and find a free decrypting solution.
- Noransom.kaspersky.com is another online source that provides ransomware decryptor and removal tools.
- Avast, Trend Micro, AVG, and McAfee too provide tools to get rid of ransomware.
Saturday 3 June 2017
Judy Malware Attacks 36.5 Million Phones — One Of The Largest Malware Campaigns on Google Play
A notorious adware named Judy had managed to break Google Play Store’s security mechanism, affecting about 36.5 million users. Judy malware spread via 41 popular apps created by a Korean company and tricked users into clicking banner ads to generate illegal revenue. After Check Point had reached out to Google, the company removed the apps from Play Store. Last week, Check Point researchers uncovered a widespread malware campaign on Google’s official app store. The notorious malware, called Judy, was found on 41 popular apps developed by a fishy Korean company.
The security researchers also found many apps other than Judy family that contained malware. The connection between the two campaigns is unclear. It’s possible that one campaign got the code from other.
Some affected apps had existed on Play Store for several years, but they were recently updated. The oldest app of the second campaign was updated in April 2016. As per Check Point’s report, it’s unclear how long the rogue code existed in the app.
How does Judy Malware operate?
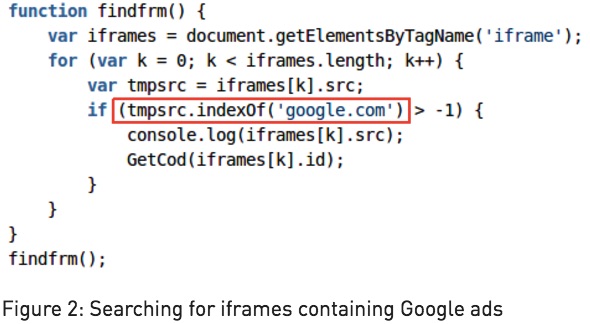
After this, Judy opened the malicious URL that imitated a PC browser in a hidden web page. It was followed by another redirection that loaded Google Ads and generated illegitimate clicks.
You can find the complete list of Judy malware apps on Check Point blog. If you’re having any of these apps installed on your Android phone due to some reason, uninstall it and use some security solution to clean your phone
Subscribe to:
Posts (Atom)